File Integrity Verification with Hashing using CertUtil
Generating and comparing file hashes to verify data integrity on Windows 11 LTSC IoT.
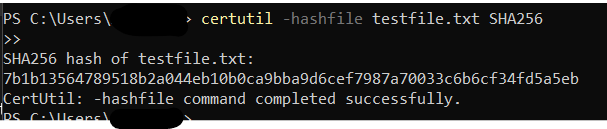 Initial SHA256 hash generation using CertUtil.
Initial SHA256 hash generation using CertUtil.
To demonstrate integrity checking using cryptographic hashes, I used CertUtil, a built-in Windows utility, to generate and verify SHA256 hashes on local files. This technique is vital in areas like forensics, secure backups, and malware detection, where detecting unauthorized changes is critical.
Test Setup
 testfile successfully created and placed.
testfile successfully created and placed.
I created a sample file named testfile.txt, inserted simple text, and then used CertUtil to generate its hash. Afterwards, I modified the file to simulate tampering, then restored it to demonstrate hash matching.
After creating the sample file, i made a copy, so that it can be tampered with:
Then i tested the hashes:
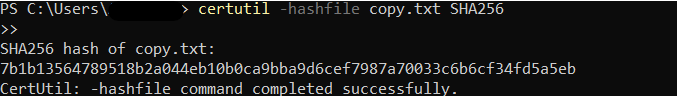 Identical SHA256 hash generation proven.
Identical SHA256 hash generation proven.
Afterwards, i tampered with the copied file, and tested the hashes again:
 Initial SHA256 hash is now different.
Initial SHA256 hash is now different.
I also tested SHA1 and SHA512.
 Different hash algorithm visible.
Different hash algorithm visible.
This project ties directly into the Security+ Domain regarding Cryptographic Concepts.
Now, i have successfully demonstrated how:
Hashes detect changes in files.
Cryptographic integrity checks are critical for verifying file authenticity.
SHA256 is a secure hashing algorithm supported by Windows natively via certutil.
Skills demonstrated:
SHA256 hashing
Detecting file integrity violations
Using native Windows tools for secure file validation
Incident response preparation (malware detection, file baselining)