Intercepting HTTP Login Credentials with Wireshark
Capturing and analyzing HTTP POST traffic containing unencrypted credentials.
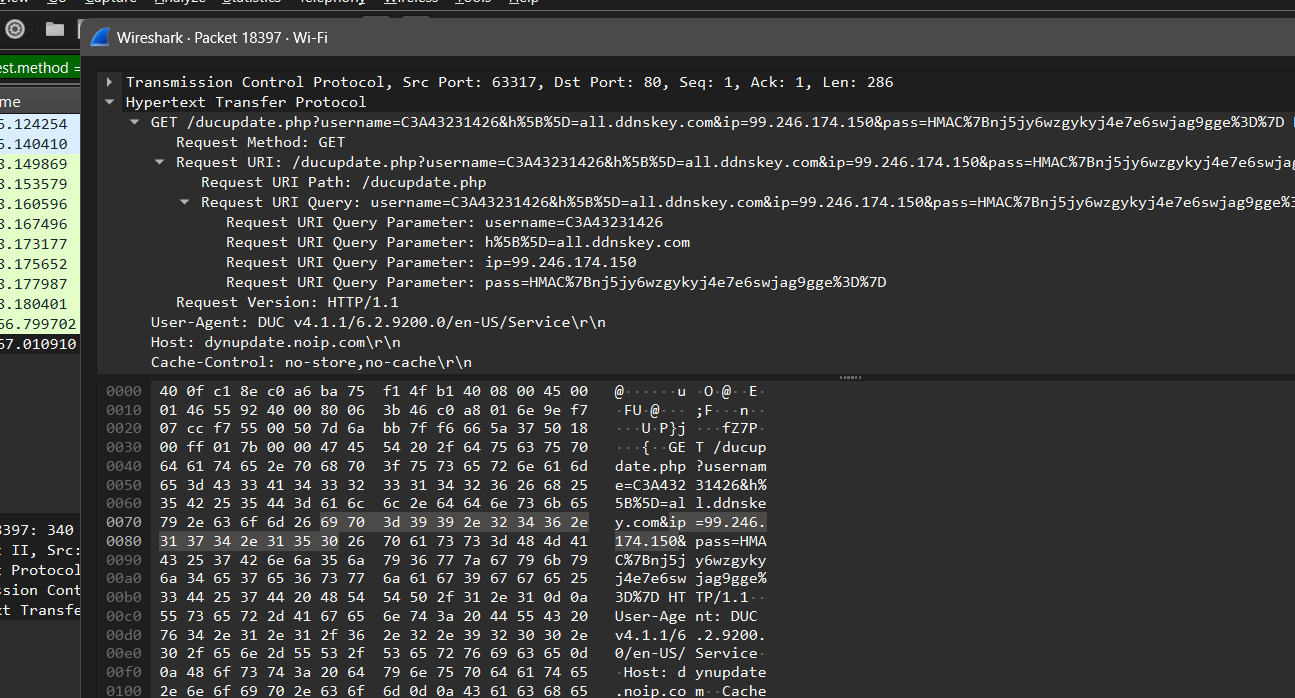 A captured POST request over HTTP showing clear-text credentials.
A captured POST request over HTTP showing clear-text credentials.
In this project, I used Wireshark to capture traffic from my browser and identified login credentials being transmitted in clear text over an insecure HTTP connection.
How It Was Done
- Started a Wireshark capture on Wi-Fi.
- Visited
http://neverssl.comto trigger unencrypted HTTP traffic. - Used the filter
http.request.method == "POST"to isolate form submissions. - Located the POST request containing form data in plain text.
Observations Made:
The captured packet showed:
POST /loginin the Info column- HTTP headers and form fields visible
username=C3A43231426andpass=HMAC%7Bnj5jy6wzgykyj4e7e6swjag9gge%3D%7Dincluded in the body
This proves that anyone intercepting this traffic could easily retrieve sensitive credentials if the site doesn’t use HTTPS.
Key Takeaway
This exercise highlights the risks of sending data over HTTP. In real-world scenarios, attackers could:
- Use packet sniffers on public Wi-Fi
- Capture credentials during form submissions
- Launch MITM attacks if HTTPS is not enforced
Modern sites must use HTTPS with proper TLS encryption to prevent this kind of data exposure.
This post is licensed under CC BY 4.0 by the author.