SSH & DNS Traffic Analysis
Analyzing SSH & DNS Traffic over a pcap file.
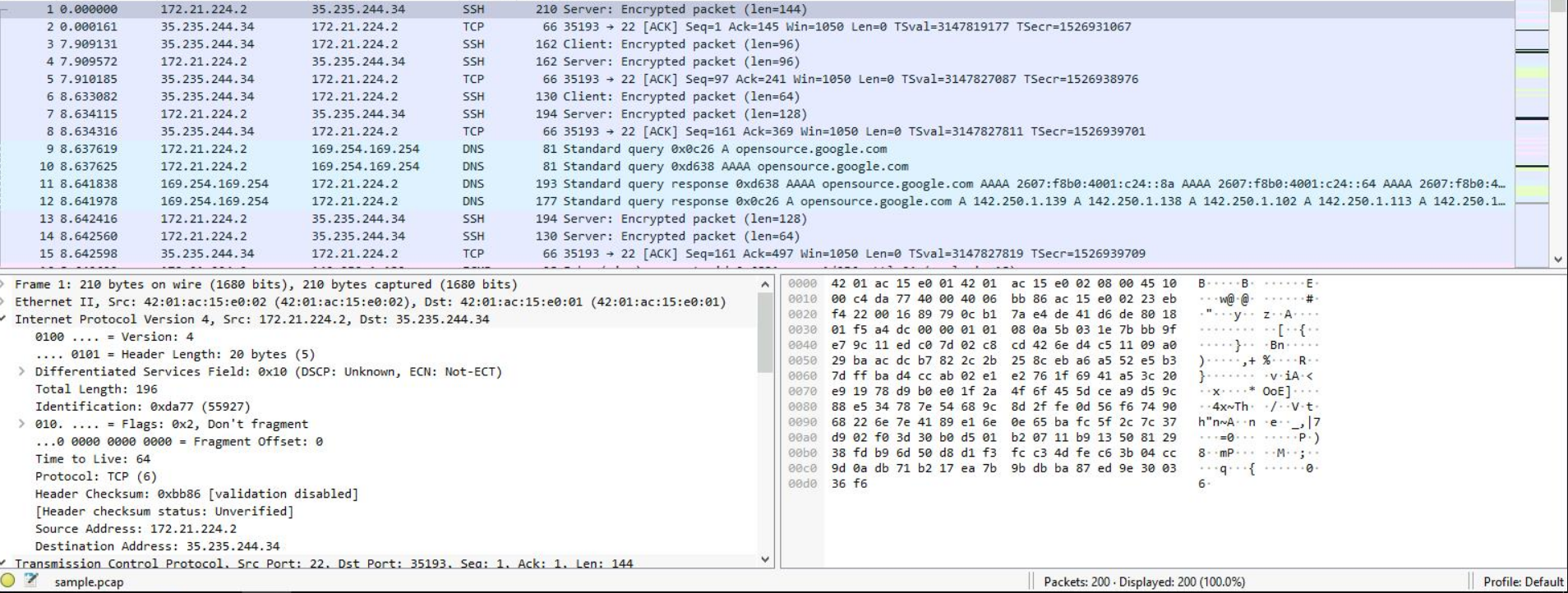 Wireshark Packet Capture screen
Wireshark Packet Capture screen
In a related analysis, I opened a .pcap file and noticed several SSH encrypted packets exchanged between a VM (172.21.224.2) and a remote IP (35.235.244.34), alongside various DNS queries to opensource.google.com.
There are some notable details we can take from this:
- Multiple TCP ACK and encrypted packets over SSH (port 22) show active secure sessions.
- DNS queries to both IPv4 and IPv6 addresses, including responses resolving to Google’s infrastructure (e.g.,
142.250.1.139), help confirm domain resolution behavior as expected. - No packet payloads are visible due to encryption, but TCP flags and sequence numbers allow traffic correlation, implying proper security.
End Use Case
This capture illustrates the mix of background activity typical on a system: DNS resolution, encrypted SSH sessions, and standard TCP behavior that is useful for baseline comparisons when hunting for anomalies, enabling us to get a proper overview of what classic packet traffic looks like through SSH and DNS being present.
This post is licensed under CC BY 4.0 by the author.